SA-CORE-2014-005 - All you need to know to protect your Drupal Site from the latest SQL Injection vulnerability
Published on October 16, 2014
Last night, Drupal Release a security update to its core - v7.32
The release addresses the SQL Injection vulnerability described at https://www.drupal.org/SA-CORE-2014-005

How serious is it?
There are many proof of concepts scripts available all over the internet now. Both python and php variants. So, anyone who is knowledgeable enough to run a php/python script can now login to your Drupal 7 Site as admin, or execute any SQL on your Drupal Database!
[I am not linking them here for the obvious reasons, if you came here searching for those scripts, you are at the wrong place]
So, is my site vulnerable?
Most of the Drupal-special webhosts like Acquia, Pantheon, Platform.sh have apparently patched their platforms protecting your Drupal site even if your individual site has not been patched yet. So most of you are safe. You should be worried if you are hosting on one of those generic hosts to whom Drupal is just yet another script or if you are running the site on your own stack. That might mitigate some attack vectors but you should still be either upgrading, or applying the patch described below.
Some CDNs like cloudflare have announced that they have updated their Web App Firewall rules to mitigate this vulnerability. So if you are using Cloudflare CDN like I do for this blog site, make sure you turn on this option. Still, this could only secure you from only some attack vectors. Should be good enough to protect your site while you upgrade. But relying on the CDN WAF rules would not be a solution and you should definitely be upgrading your site or apply the patch described below.
In short, if you haven’t upgraded to 7.32 or if you haven’t applied the patch yet, your site is vulnerable and you should fix it.
How do I fix my Site?
Don’t worry. Fortunately it is very simple. And it would not take more than 2 minutes to fix your site (if you do it via #3 below).
If the words like “git”, “patch”, “upgrade” scare you and if you like the words “FTP”, “Filezilla” more then skip directly to #3 below.
-
OPTION #1: The first option is to update your site to the latest version of Drupal - 7.32. If you are already on 7.31, this should be pretty smooth since the difference between 7.31 and 7.32 is just the fix for this issue and hence might not even require as much of regression testing as you would need with usual upgrades.
-
OPTION #2: If you are far behind 7.31 and if you would need time to upgrade and test your site, then you should consider applying this patch immediately, even before you upgrade.
Patch : https://www.drupal.org/files/issues/SA-CORE-2014-005-D7.patch
How do I apply this patch?
Like any other patch -
- SSH To your drupal root directory
- Get the patch by executing the command
wget http://www.drupal.org/files/issues/SA-CORE-2014-005-D7.patch - Assuming you got git on the server, run the command
git apply -v SA-CORE-2014-005-D7.patch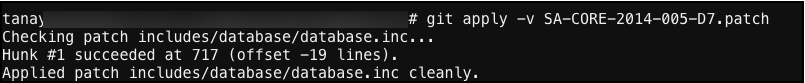 If you see something like this, you are all set now :-)
If you see something like this, you are all set now :-)
-
OPTION #3: [THE SIMPLEST OF ALL] Alternatively, if you do not want to deal with patches or upgrades, or if you are are looking for a quick fix, here you go:
- FTP to, or open your Drupal Root Directory
- Navigate to includes/database/ folder
- There will be a file named database.inc . Take a backup of the file. We are going to modify the file. Store the backup somewhere safe just in case.
- Open the file database.inc .
- At around line 739, you will find a line of code that reads
foreach ($data as $i => $value) { - Replace this line with
foreach (array_values($data) as $i => $value) { - Save the file and exit
- Pat yourself on the back. You are all set now :-)
I have no enemies. Should I still fix my site?
Absolutely yes. With the many google dorks that could be used to find Drupal Sites, you could be the subject of random attack. - ie Some noob with the script picking up your site randomly to login as admin and defacing it or playing around with it, or stealing your userbase for spamming!
Who found this issue? Who reported it? When was it first reported? ……. Check out the FAQ on Drupal.org for answers - https://www.drupal.org/node/2357241